Access Control List(ACL)
Access Control List
Earliest Method of providing network security.
It provides layer 3 and layer 4 security.
Controls the flow of traffic from one network to another.
Filter packets (packet filtering firewall)
Terminologies
- Deny: blocking a network/Subnet/Host/Service
- Permit: Allowing a network/Subnet/Host/Service
- Source Address: The address from where the request starts.
- Destination Address: The address where the request sends.
- Inbound: Traffic coming into the interface
- Outbound: Traffic going out of the interface
- Protocols:
- IP(Internet Protocol)
- TCP (Transmission Control Protcol)
- UDP (User Datagram Protocol)
- ICMP (Internet Control Messaging Protocol)
- eq(equal to)
- neq(not equal to)
- lt(less than)
- gt(greater than)
Wildcard Mask
- Tells the router which addressing bits must match to the address given in the ACL statement.
- It is the inverse of subnet mask, hence is also called as inverse mask.
- A bit value of '0' indicates must match.
- A bit value of '1' indicates IGNORE(ignore bits)
- Wildcard mask for a host will be always 0.0.0.0
Working of ACL
- Works in a sequential order from top to bottom.
- If a match is found it does not check further
- There should be at least one permit statement.
- An implicit deny blocks all traffic by default when there is no match(an invisible statement)
- New entries are automatically added to the bottom
- Can have one access list per interface per direction.
- Removing of specific statements in ACL is not possible (need to remove entire list, then create.)
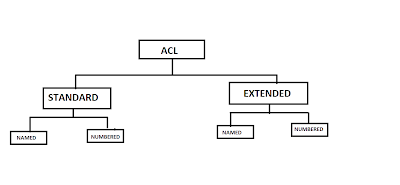
TYPES OF ACL
Standard ACL
- The access list number range is 1-99
- Can filter a network, subnet or host.
- Two way communication is stopped.
- All services are blocked or allowed
- Filters traffic based only on the source address
- Implemented closest to the destination(Guideline)
Creation:
Syntax:
Router(Config)#access-list <acl no> <permit/Deny> <source address> <source wildcard mask>
Implementation:
Router(config)#interface <interface type> <interface no>
Router(config-if)#ip access-group <number> <out/in>
Verification:
Router#show ip access-list
Extended Access List
- The access-list number range is 100-199
- Can filter a network, subnet, host and service.
- One way communication is stopped.
- Selected services can be blocked or allowed
- Filters traffic based on the source address, destination address and service.
- Implemented closest to the source(Guideline).
Creation:
syntax:
Router(config)#access-list <aclno> <permit/Deny> <protocol> <source address> <destination wildcard mask> <operator> <service>
Implementation:
Router(config)#interface <interface type> <interface no>
Router(config-if)#ip access-group <number> <out/in>
Verification:
Router(config)#show ip access-list
Extended Access control list configuration video
Extended Access control list configuration video
sql azure training
ReplyDeletevmware training
ServiceNow Online Training